Subaccount and Group Management
An overview of creating subaccounts and groups for accessing ChaosSearch
ChaosSearch includes built-in authentication and authorization controls that allow the primary user to create and manage subaccounts and groups. There are console user interfaces as well as API endpoints for managing subaccounts and groups. There are also sample RBAC templates to help with the definition of permissions for different user types.
Subaccount Management
Primary users can define static subaccounts using the Users page. (The Accounts menu is not visible to subaccount users.) A sample Accounts > Users page follows:
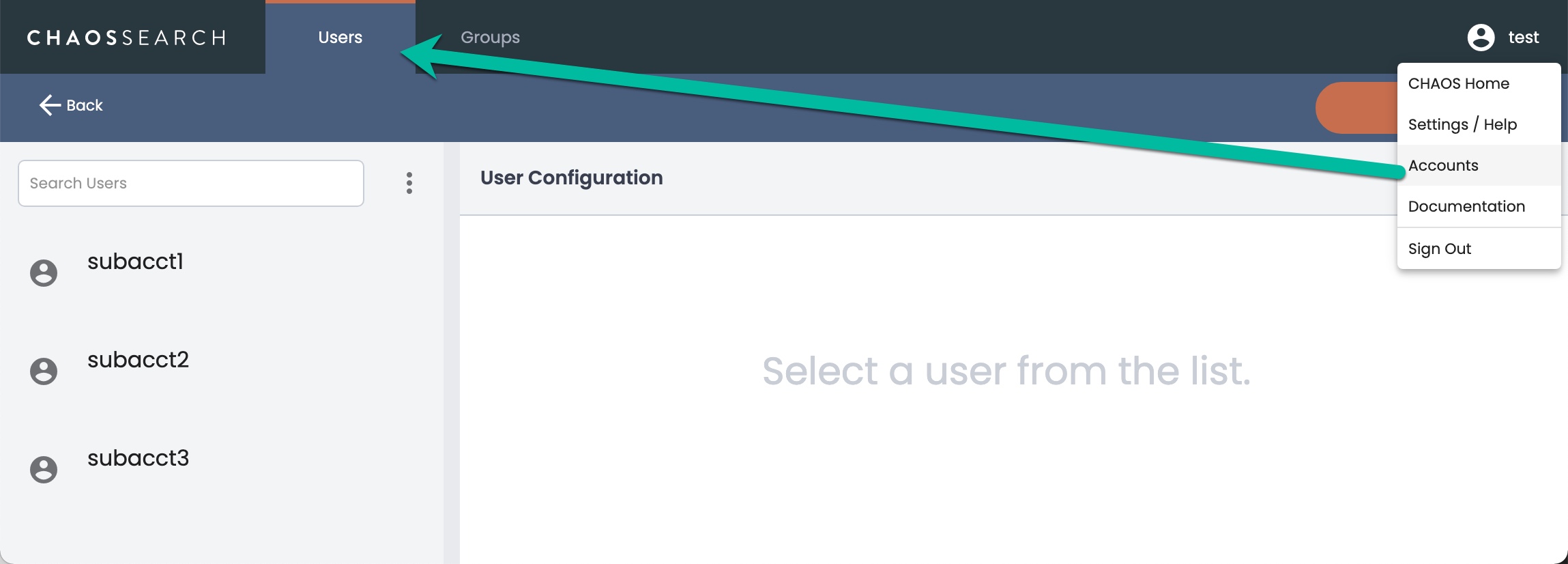
The Users page shows only subaccounts, never the primary user information.
Group/Role Management
The group roles are permissions that authorize the use of specific features and access to specific types of information. Primary users can use the Groups page to define roles that control which buckets, object groups, and views can be accessed, whether the user has permission to create and manage object groups or views, and access to the UIs like Search Analytics and SQL Analytics.
Local Groups Are Used for SSO User AuthorizationEven for sites that use SSO to authenticate their users and grant ChaosSearch access, locally defined groups in ChaosSearch are required to specify the various permissions and authorizations for users. The SSO users are typically granted access to (or revoked from) the group names at their SSO site.
The group names at the SSO must match exactly the locally defined groups inside ChaosSearch to ensure that the correct permissions are applied within ChaosSearch. As an example, a trailing space character for a ChaosSearch group name resulted in a mismatch with the group name passed in an SSO request, blocking the authorization to ChaosSearch features. Be sure to carefully check the entire group name character composition.
Subaccount users can be associated with one or more groups to grant that user the set of permissions associated with the groups. A sample Accounts > Groups page follows with the default group and a user-created group called viz_user:
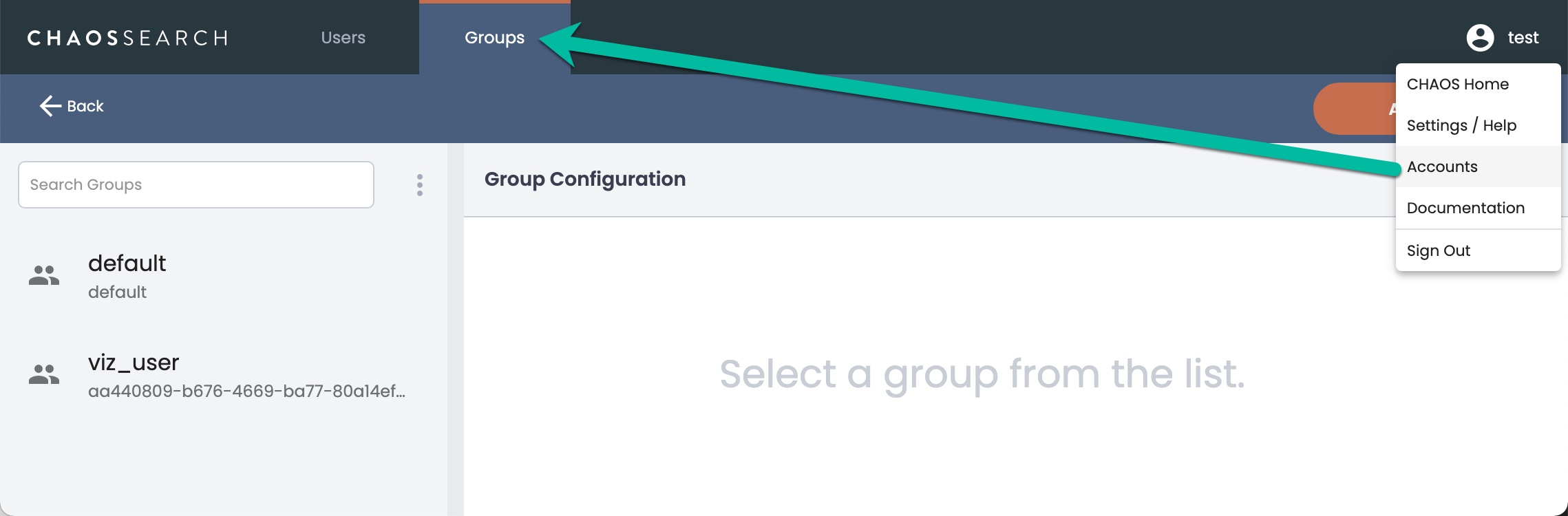
Primary users can create groups using the Groups UI and by specifying the RBAC permissions as blocks of values for the group, or by importing a JSON file of permissions and rules. See Recommended RBAC Group Setups for an example of a common group model.
About the default Group
The default group starts with administrative-level permissions, which are useful during the limited access initial trials of ChaosSearch but not typically the permissions that customers would assign to new or auto-provisioned users in production environments.
As a best practice when you start to create more specific groups, change the settings of the default group to reflect the minimal permissions that a new user should be granted. If the default group settings are not modified, new or auto-provisioned users could have more UI and administration privileges and access to see all object groups and views.
Updated 9 months ago
