S3 Troubleshooting
A summary of different approaches for troubleshooting S3 access
This topic provides some S3 troubleshooting guidance for topics about the levels of access needed for ChaosSearch to index log and event files stored in one or more of your AWS S3 buckets.
Read Access for S3 Objects
If you are unable to Preview or Index objects in the ChaosSearch UI, you might not have the appropriate level of access needed to view this object. A common reason is that the object is owned by another AWS account.
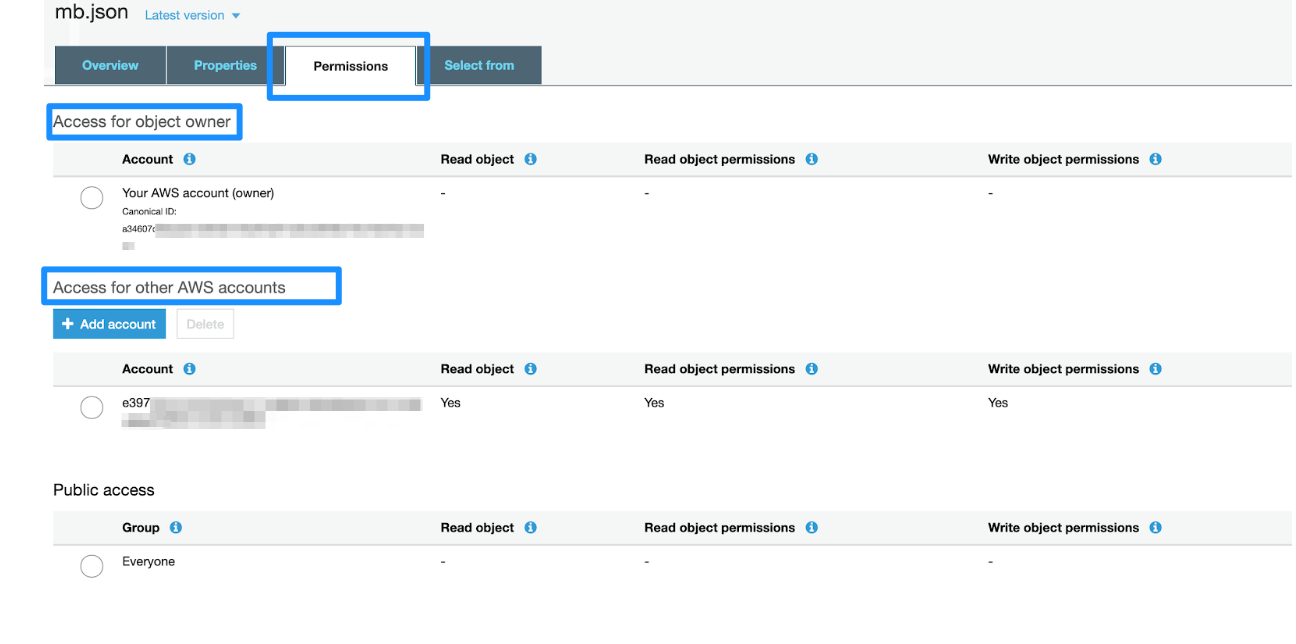
In this example, the S3 bucket owner has read object and write object permissions (full perms) and can read the object. This object is in a bucket owned by e397 but the object is owned by a34607. The bucket owner does not have the appropriate level of permissions on the object.
This is different for a file owned by the S3 bucket owner.
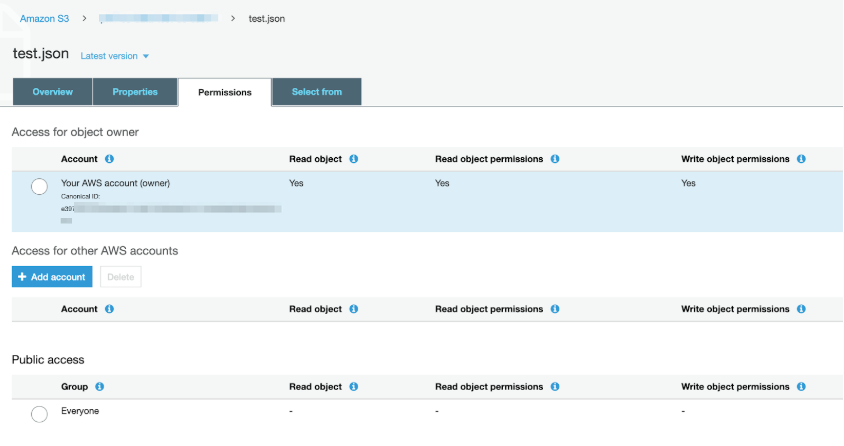
Troubleshooting – Who owns the S3 Object
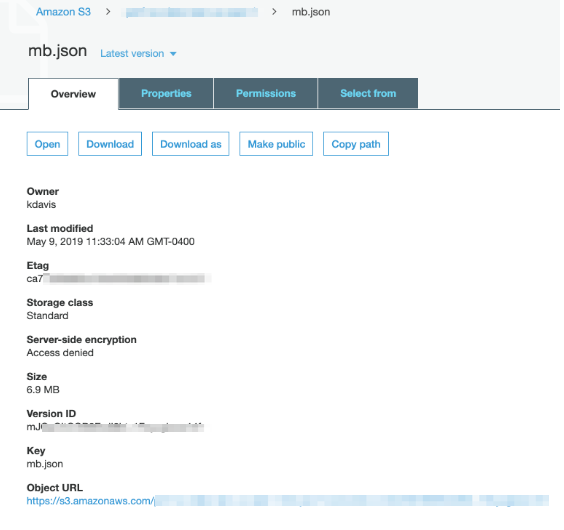
The AWS Overview tab has information on the account" that owns the object. Note the Access denied for server-side encryption. As a result, only the object owner can read some metadata about the object.
If you would like to change the object owner, you can change the ACL on the object uploaded to the S3 bucket to give the bucket owner full permissions.
aws --profile userexample s3api put-object-acl --bucket name-of-s3-bucket --key mb.json --grant-full-control id="canononical-id"S3 Policy – No Upload Authority
This IAM Policy example does not allow the upload of files that are not owned by the bucket owner.
{
"Version": "2012-10-17",
"Id": "Policy1557350455933",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789:user/user.name"
},
"Action": "s3:*",
"Resource": "arn:aws:s3:::your-s3-bucket/*"
},
{
"Effect": "Deny",
"Principal": {
"AWS": "arn:aws:iam::123456789:user/user.name"
},
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::your-s3-bucket/*",
"Condition": {
"StringNotEquals": {
"s3:x-amz-grant-full-control": "id=canonical-id"
}
}
}
]
}Updated 10 months ago
