About Single Sign-On
ChaosSearch provides users with a straightforward integration to common SSO services.
In addition to its local authentication and authorization support, ChaosSearch supports single sign on (SSO) integrations with popular identity identity provider (IdP) services such as Auth0, Okta, Google, Azure AD, and others to authenticate and authorize user access. ChaosSearch authentication uses the recommended Authorization Code Flow with Proof Key for Code Exchange (PKCE).
ChaosSearch supports two models of SSO logins: Our recommended service-provider initiated model (SP-initiated), and a bookmark-style model where users can connect to ChaosSearch from their IdP portals.
Direct IdP-initiated logins are not supported.With the change to ACF-PKCE authentication, support for direct IdP-initiated logins is deprecated, per the guidance from the IAM and IdP community.
These topics describe the ChaosSearch SSO models.
Overview of ChaosSearch SP-Initiated SSO Model
In the ChaosSearch service provider (SP) authentication model, users who connect to the ChaosSearch portal initiate a login authentication process as follows:
- User accesses the ChaosSearch login page and clicks Single Sign On.
-
ChaosSearch redirects to its Auth0 broker through a secure TLS tunnel.
-
Using its ChaosSearch-configured connectors, Auth0 sends a request to the customer's configured SAML IdP connector to authenticate the user.
-
After the user authenticates, the IdP responds to Auth0 with an authentication SAML response/JWT token in the browser.
-
Auth0 sends the proof of key/code exchange token in the browser to ChaosSearch, which uses the information to process and complete the authentication and authorization to the configured ChaosSearch tenant.
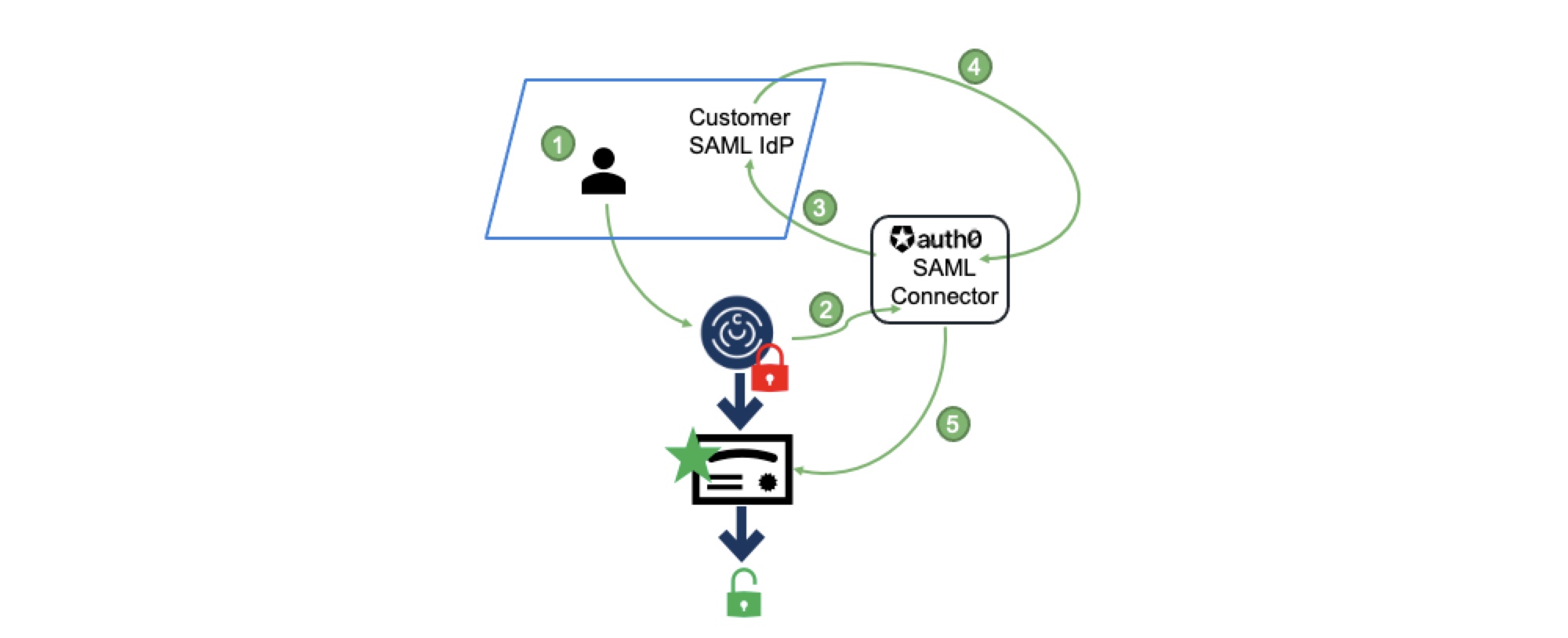
To configure the SP-initiated model, there are required configuration steps and information handoffs between ChaosSearch and the customer IdP admins to set up the connection from the ChaosSearch login page Single Sign On button, through Auth0, to the customer's IdP and back through Auth0 to the ChaosSearch tenant instance.
Overview of ChaosSearch IdP Bookmark Authentication Model
Some customers might prefer for their users to log in and authenticate with their company's identity provider (IdP) first, and then be allowed to connect to and access ChaosSearch. This is a form of identity provider (IdP) initiated authentication. As noted earlier in this topic, ChaosSearch does not support direct IdP-initiated logins with our ACF-PKCE based configuration, but there is some support for an alternative that uses IdP bookmarks or apps.
The bookmark-style model offers a similar experience where users first log in to their IdP for authentication, and then click a bookmark or other icon on their IdP portal to access ChaosSearch if permitted:
-
The user logs in and authenticates with their organization's IdP service.
-
Permitted users click a bookmark, link, or application icon (the mode varies depending on the IdP) to access ChaosSearch.
-
The user's IdP connects to Auth0 and submits the information to request access to ChaosSearch.
-
Auth0 verifies the user access request, and sends JWT access information to ChaosSearch, which will verify the information and grant access to the ChaosSearch console.
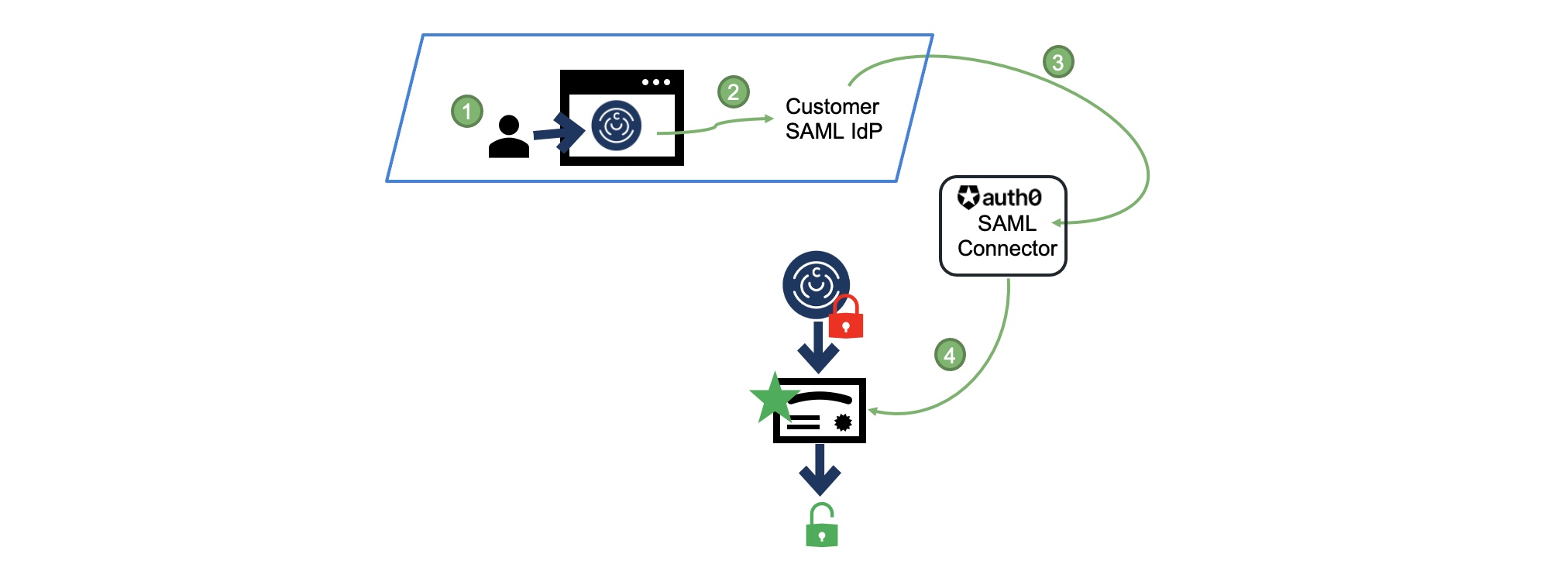
Just like the SP-initiated model, the bookmark-based IdP model requires some configuration steps and information handoffs between ChaosSearch and the customer IdP admins to create the connections. In addition, the IdP admins must create links to the ChaosSearch service within the user portals, and grant specific users or groups access to those links, so that permitted users can authenticate locally and then connect to ChaosSearch from their portal (rather than going to to the ChaosSearch login page), as in the following example for JumpCloud:
Carefully consider IdP-initiated authentication and securityAn IdP-initiated authentication might be more convenient for users because they have a ChaosSearch link or icon on their main end-user portal for all their applications. Be sure to note the well-documented security concerns raised by IAM vendors, such as vulnerability to login cross-site request forgery (CSRF) attacks and man-in-the-middle attacks. If you choose an IdP-initiated authentication model for ChaosSearch, make sure that you are aware of the possible security concerns for this mode.
Benefits of Single Sign-On
Using SSO solutions offers the following benefits versus locally defined users and groups:
Reduced password fatigue: Remembering one less password. Users of your organization who are granted access to ChaosSearch do not need to create and remember another password for ChaosSearch to log in and use our features.
Easily manage user access: Administrators can grant/prohibit access to ChaosSearch for their users via their IdP console without having to manage separate user accounts in ChaosSearch. Administrators have less application overhead for managing users and easier overall access control management for changes.
Improved security: Your identity provider manages and sends authentication assertions when users are authenticating to ChaosSearch, instead of passwords that are created by users.
Updated 10 months ago
