Husk Users
For SSO authenticated sites, read about the concept of husk users.
With SSO authentication, ChaosSearch has two models for representing the subaccount users: just in time (JIT) users and husk (ephemeral) users.
ChaosSearch includes support for an SSO-authentication model where the subaccount user and group assignments are both managed in the IdP. There is no permanent local subaccount created inside ChaosSearch for the user. This is referred to as a husk or ephemeral user configuration.
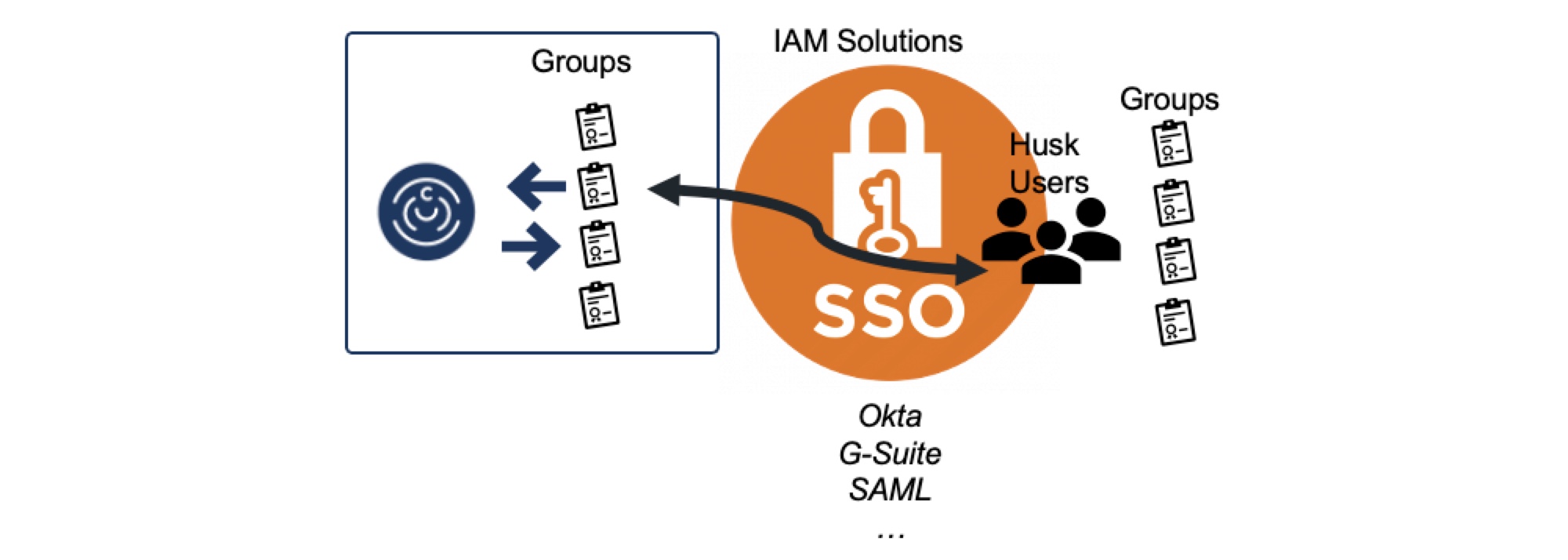
When a subaccount user authenticates in the IdP, the IdP passes both the authentication and authorization (assigned group information) to ChaosSearch.
ChaosSearch creates a husk (ephemeral) subaccount for the SSO user to support the access connection. The group information passed with the login message is matched with the locally defined groups in ChaosSearch to configure the authorizations for the husk user. The groups must exist in ChaosSearch, and the IdP service must specify the group names exactly as they appear in ChaosSearch, otherwise the husk user might have no authorizations within ChaosSearch.
The husk subaccounts are not shown on the ChaosSearch Users page, and the ephemeral account is removed when the SSO user logs out of the ChaosSearch environment. Husk users offer the benefits of managing the user authentication and group assignments within the IdP (bypassing the subaccount creation and group assignment tasks in the ChaosSearch interface). Also, the husk users are not listed on the Users page, which might be a desired security benefit for some customers.
The major advantage of husk users is the minimal footprint. Unlike with static or auto-provisioned auto-provisioned users, when a user is removed from the IdP provisioning, or if a user is revoked from ChaosSearch access, there is no subaccount remnant on the ChaosSearch primary to remove.
Updated 10 months ago
