ChaosSearch User Authentication and Authorization
Read about the user and group role-based access controls (RBAC)
ChaosSearch offers strong security controls with built-in interfaces and APIs to manage subaccounts and to define their roles (access) to features and information. ChaosSearch also supports single sign on (SSO) integrations with identity providers (IdPs) such as Auth0, Okta, Google, and others to authenticate and authorize user access to the interface, features, and customer data. The following topics describe the authentication and authorization methods in ChaosSearch.
Primary User and Subaccounts
Each ChaosSearch deployment has a primary user (also called a tenant or root account), which is essentially the owner/superuser associated with the ChaosSearch setup and deployment. The primary user can perform all of the administration and related tasks for their environment, including user and group management.
The primary user can create and manage subaccounts and groups to create independent login accounts and to grant those users specific access to the ChaosSearch interfaces, tasks, object groups, and views.
ChaosSearch also supports integrations with many popular single-sign-on solutions (SSOs) to support customers who manage authentication and authorization using Identity Providers (IdPs).
Login Page
The ChaosSearch login page highlights the types of supported user authentication services. This page displays when users connect a web browser to their ChaosSearch domain such as https://mycompany.chaossearch.com.
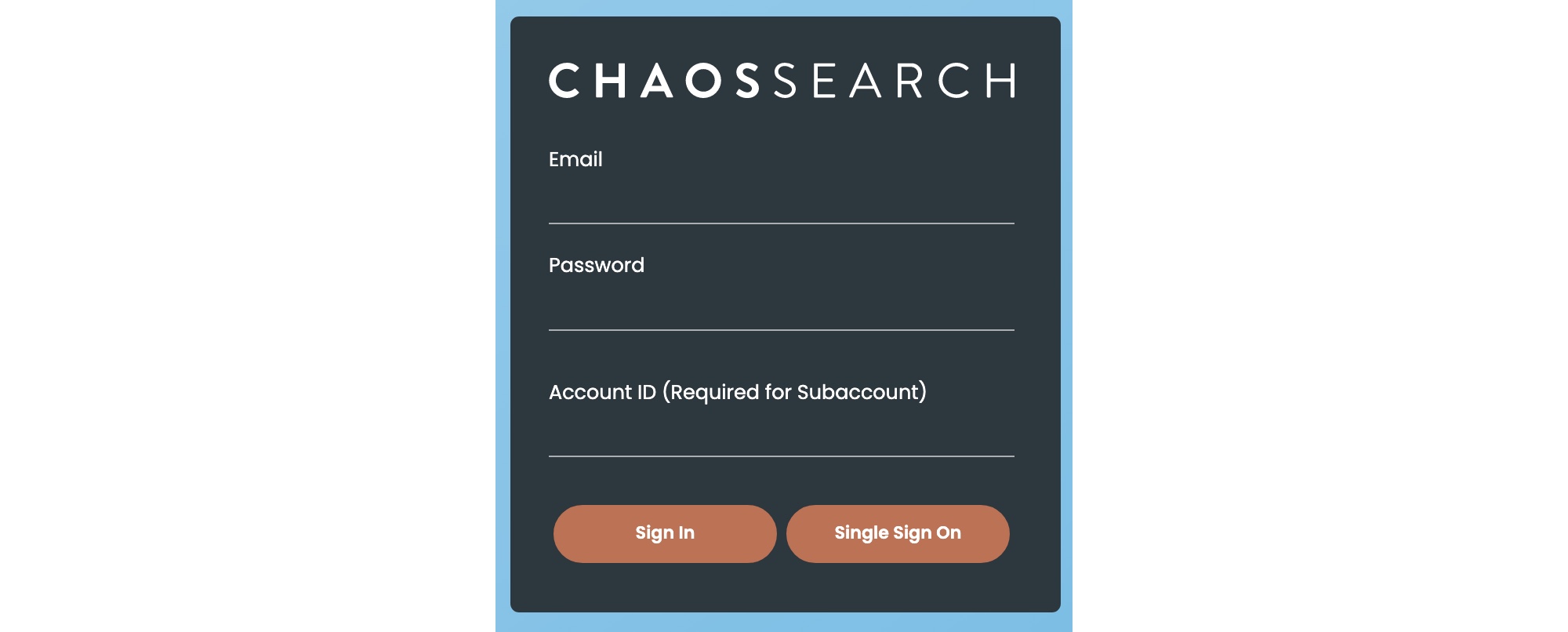
To log in, primary users type their email account information that was specified for the ChaosSearch deployment, their password, and click Sign In.
Subaccount users must specify their configured email and password, and also the Account ID of the parent user (that is, the external ID for the ChaosSearch user deployment as defined on the Credentials page). A subaccount could be associated with one or more primary users, so the primary ID must be supplied as part of the login.
Single Sign On Support
For SSO environments, users click Single Sign On to redirect the login to their configured IdP for authentication. After authenticating, they are returned to ChaosSearch with their authorizations. This is referred to as the SP-initiated model.
Customers who have a configured identity provider (IdP) for authenticating their users via single sign-on (SSO) often prefer to use their IdP to authenticate their subaccount users and to authorize access to application services. In this case, users and groups are typically defined within the IdP broker, authenticated at the IdP, and then their authorization credentials are passed to ChaosSearch.
ChaosSearch offers two SSO configuration behaviors:
- ChaosSearch could automatically create subaccounts to represent those IdP-managed users. The subaccounts are still managed by the IdP, but there is a local subaccount created in parallel in ChaosSearch.
- When SSO users do not have a corresponding subaccount within ChaosSearch, they are referred to as ephemeral or husk users.
For either method, there must be locally defined ChaosSearch user groups that define the authorizations granted to the subaccounts.
SSO From Bookmarks
Another common SSO practice is for customer administrators to create bookmarks or other link connections within their IdP company portals or pages. This is referred to as the IdP-initiated model. As an alternative to navigating to the ChaosSearch Login page and clicking Single Sign-On in the SP-initiated model, users will navigate to the links or bookmarks defined within their organization's SSO portal pages (such as JumpCloud, Azure, or Okta) that connect to ChaosSearch from within their authenticated environment. See Configuring Single Sign On and contact Customer Success for more information.
Updated 9 months ago
