Just in Time Users
For SSO authenticated sites, read about the concept of JIT users.
With SSO authentication, ChaosSearch has two models for representing the subaccount users: just in time (JIT) users and husk (ephemeral) users.
In the just-in-time (JIT) auto-provisioning model, when a subaccount user connects via SSO provisioning for the first time, ChaosSearch automatically creates a local subaccount if one does not already exist. The new subaccount is automatically configured with access to a group named default. The SSO user is associated with their local JIT user account to establish access to ChaosSearch.
NOTEIf there is already a matching, static subacccount in ChaosSearch for the SSO user, the system uses that existing subaccount, and also uses its current group provisioning for authorizations.
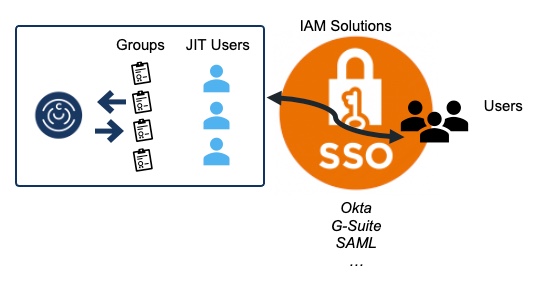
As an important consideration for JIT users, ChosSearch admins must manage the user and group assignments locally for JIT users. Also, when users are removed or deactivated from the customer IdP, the ChaosSearch admin must manually remove the corresponding JIT account from ChaosSearch.
JIT Users and the default Group
default GroupThe default group starts with administrative-level permissions in a new environment. A full range of permissions is typically helpful for initial or trial setups, but over time, such a wide range of access is usually not desired. As a best practice, customer administrators should change the settings of the default group to reflect the permissions that a new JIT user should be granted. If the default group is not modified, the administration privileges are granted to JIT users or any new users with default access.
Customer administrators can change the auto-provisioned/JIT subaccounts to assign different groups and to manage the accounts as needed. Note that group assignment changes might require an authenticated JIT user to log out of ChaosSearch and re-authenticate to obtain the updated group assignments.
Updated 10 months ago
