CloudFormation Access Provisioning
Use CloudFormation as a programmatic way to provision access for ChaosSearch.
AWS CloudFormation is a provisioning and configuration service that can ease AWS access and configuration. ChaosSearch offers a CloudFormation template to help automate the steps to provision ChaosSearch access to your AWS cloud storage buckets. This process creates an AWS role and AWS policy in your environment for ChaosSearch to have list read-access to one or more of your S3 buckets where log and event files are stored.
Getting Started
The prerequisites required for this section are:
- A configured ChaosSearch cluster (so that you have an account and external ID)
- An AWS account for your cloud environment
Using the CloudFormation Access Setup
To use CloudFormation to set up access for the ChaosSearch indexing services:
- Log in to the ChaosSearch console using your account.
- Click your account name in the top right corner, and select the Settings/Help menu.
- Click AWS Credentials in the left menu.
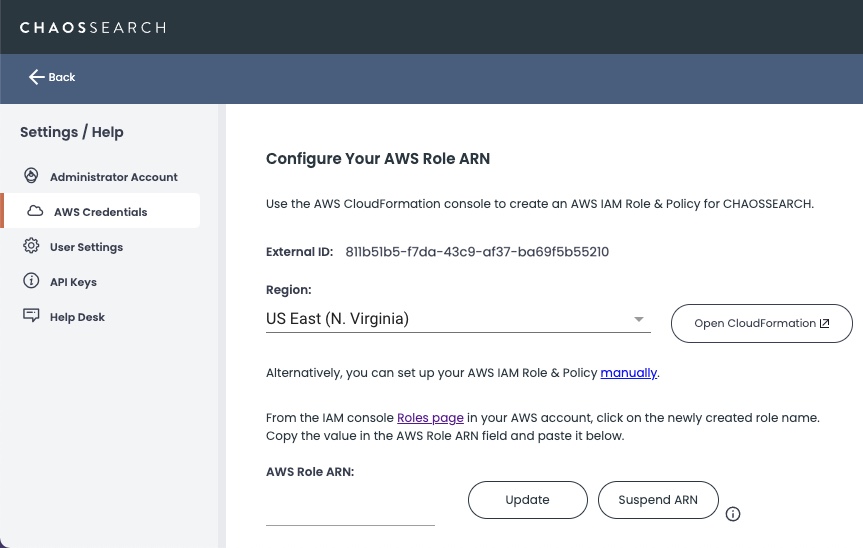
- On the AWS Credentials page, click Open CloudFormation.
- Log in using your AWS account. The Quick create stack page appears.
- In the Stack name field, type a unique stack name for your setup such as
mycompany_chaossearch.
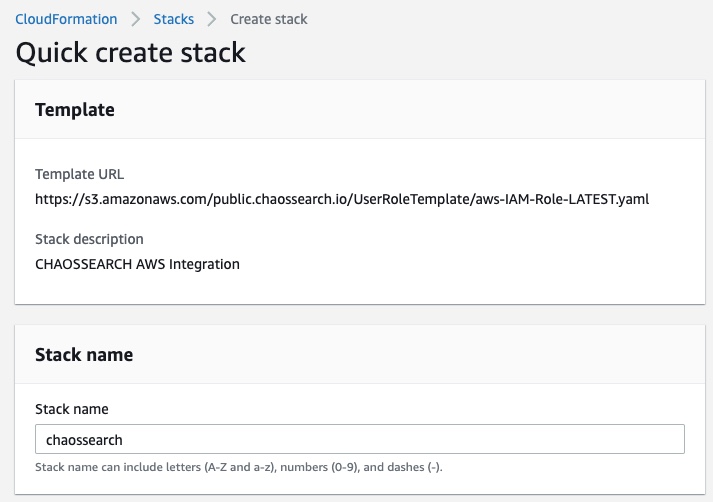
- Scroll down to the Parameters section and specify/verify the following information:
- Verify or specify (if not present) the external ID for your ChaosSearch instance. The external ID loads automatically when you launch CloudFormation from the AWS Credentials page.
- In the CSAccountID field, verify or specify your account ID. The CSAccountID loads automatically when you launch CloudFormation from the AWS Credentials page.
- In the CSBucketName field, type the name(s) of your S3 bucket(s) that contain the log and event files that you want to index. You can type one or more specific bucket names (recommended), bucket names with a path prefix, or the value
*to grant ChaosSearch read access to all buckets (not recommended). For more information about bucket naming options, see IAM Role Policy Permissions. - In the CSRecoveryAccountID, note the recovery account ID used for backup and possible recovery of the primary account. The external ID loads automatically when you launch CloudFormation from the AWS Credentials page.
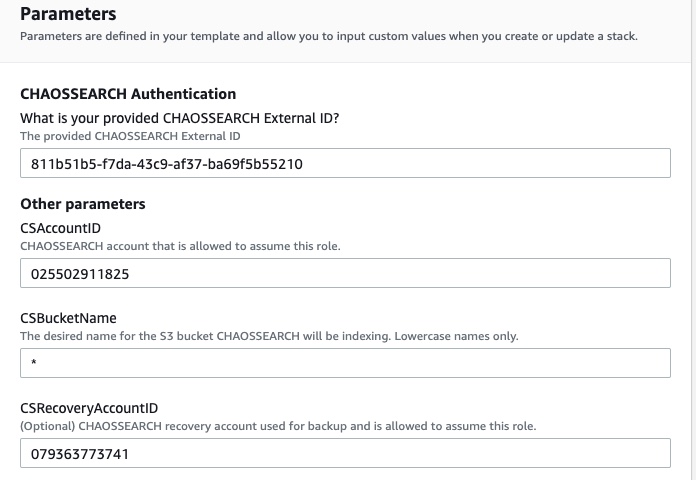
- Scroll to the Capabilities section and select I acknowledge that AWS CloudFormation might create IAM resources.
- Click Create stack.
AWS creates the ChaosSearch stack for your resources. A sample stack window follows.
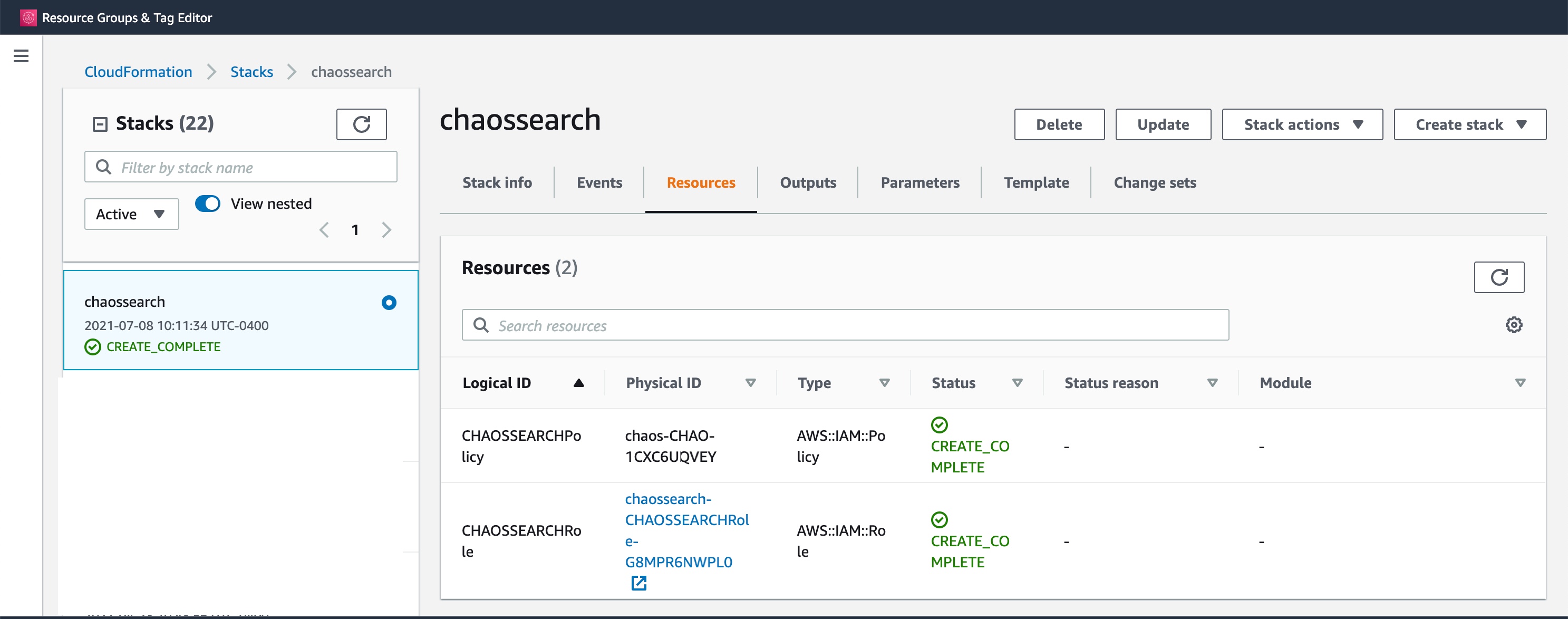
- Click the Resources tab and wait for the stack to be created.
NOTE: If the create stack process fails, contact ChaosSearch Customer Success for assistance. - Once complete, click the Physical ID hyperlink for CHAOSSEARCHRole. The Summary page appears.
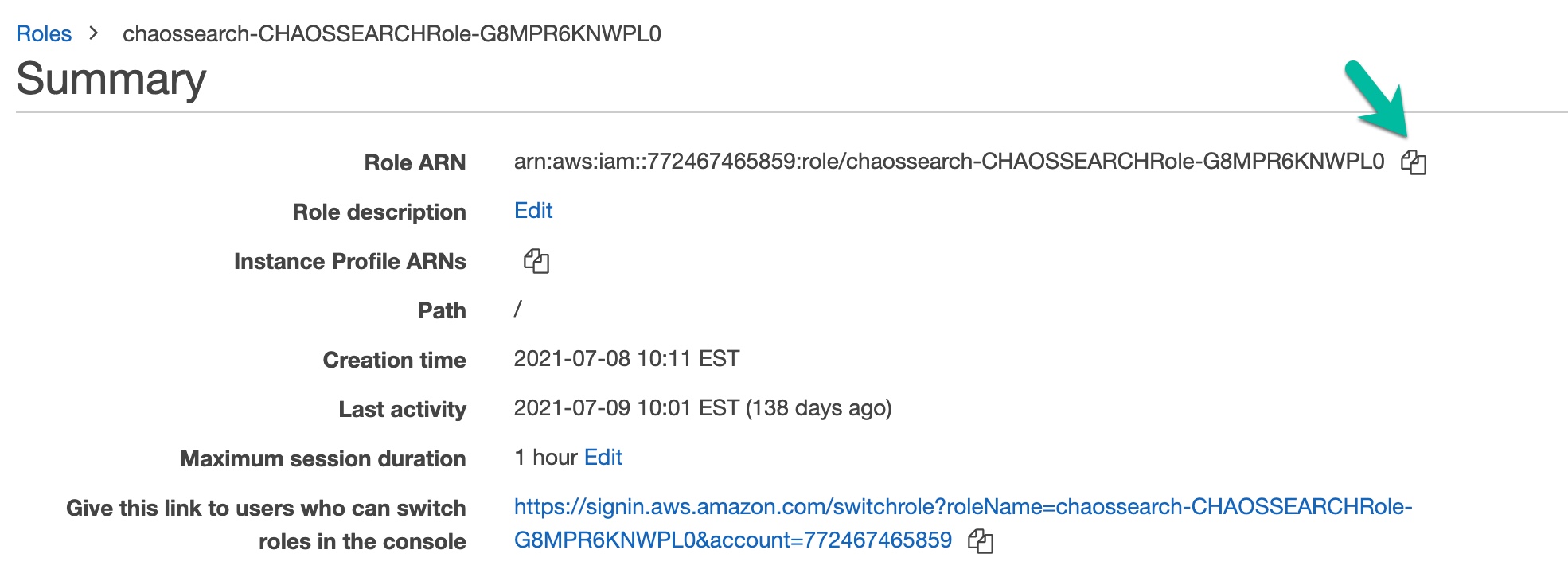
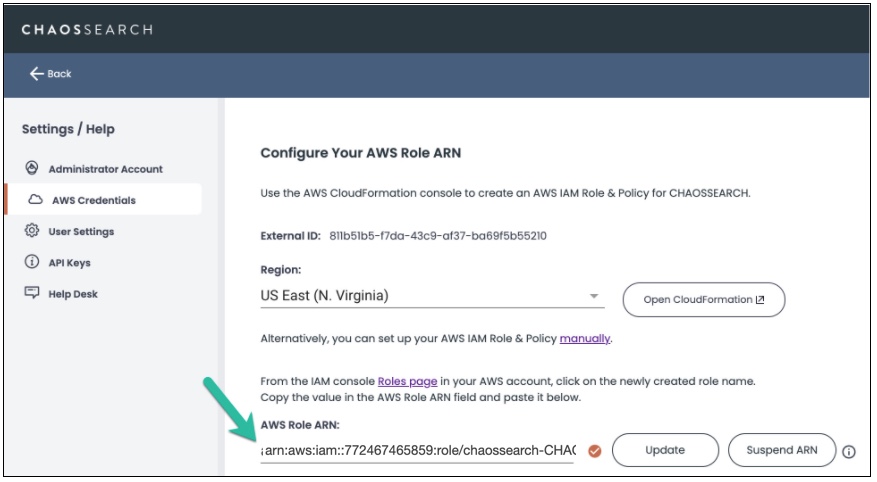
- Copy the Role ARN for your new AWS access policy stack.
- In the ChaosSearch Settings/Help > AWS Credentials window, paste the role ARN value into the AWS Role ARN field.
- Click Update to save the role ARN.
- Make sure that a check icon is displayed to verify the ARN value.
CloudFormation Template
The ChaosSearch AWS CloudFormation access policy template is available in the AWS repositories. The template has the following content:
---
AWSTemplateFormatVersion: '2010-09-09'
Description: CHAOSSEARCH AWS Integration
Metadata:
AWS::CloudFormation::Interface:
ParameterGroups:
- Label:
default: CHAOSSEARCH Authentication
Parameters:
- CSExternalID
ParameterLabels:
CSExternalID:
default: What is your provided CHAOSSEARCH External ID?
CSBucketName:
default: What bucket for CHAOSSEARCH access?
CSAccountID:
default: CHAOSSEARCH account that is allowed to assume this role.
CSRecoveryAccountID:
default: (Optional) CHAOSSEARCH recovery account used for backup that is allowed to assume this role.
Parameters:
CSExternalID:
Description: The provided CHAOSSEARCH External ID
Type: String
CSBucketName:
Description: The desired name for the S3 bucket CHAOSSEARCH will be indexing. Lowercase names only.
Type: String
CSAccountID:
Description: CHAOSSEARCH account that is allowed to assume this role.
Type: String
CSRecoveryAccountID:
Description: (Optional) CHAOSSEARCH recovery account used for backup and is allowed to assume this role.
Default: "079363773741"
Type: String
Conditions:
RecoveryDisabled: !Equals [!Ref 'CSRecoveryAccountID', '']
Resources:
CHAOSSEARCHRole:
Type: AWS::IAM::Role
Properties:
AssumeRolePolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Principal:
AWS:
Fn::If:
- RecoveryDisabled
- - Fn::Join:
- ''
- - 'arn:aws:iam::'
- Ref: CSAccountID
- ':root'
- arn:aws:iam::515570774723:root
- - Fn::Join:
- ''
- - 'arn:aws:iam::'
- Ref: CSAccountID
- ':root'
- Fn::Join:
- ''
- - 'arn:aws:iam::'
- Ref: CSRecoveryAccountID
- ':root'
- arn:aws:iam::515570774723:root
Action: sts:AssumeRole
Condition:
StringEquals:
sts:ExternalId:
Ref: CSExternalID
CHAOSSEARCHPolicy:
Type: AWS::IAM::Policy
Properties:
PolicyName: CHAOSSEARCHPolicy
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Action:
- sqs:DeleteMessage
- sqs:DeleteMessageBatch
- sqs:ReceiveMessage
- sqs:GetQueueUrl
- sqs:GetQueueAttributes
Resource: !Sub 'arn:aws:sqs:*:${AWS::AccountId}:*'
- Effect: Allow
Action:
- s3:ListAllMyBuckets
- s3:GetBucketLocation
- s3:GetBucketTagging
Resource: "*"
- Effect: Allow
Action:
- s3:ListBucket
Resource:
- Fn::Join:
- ''
- - 'arn:aws:s3:::'
- Ref: CSBucketName
- Effect: Allow
Action:
- s3:GetObject
- s3:GetObjectTagging
- s3:PutObjectTagging
Resource:
- Fn::Join:
- ''
- - 'arn:aws:s3:::'
- Ref: CSBucketName
- "/*"
- Effect: Allow
Action:
- s3:GetObjectTagging
- s3:PutObjectTagging
- s3:ListBucket
- s3:CreateBucket
- s3:GetObject
- s3:PutObject
- s3:DeleteObject
Resource:
- Fn::Join:
- ''
- - 'arn:aws:s3:::cs-'
- Ref: CSExternalID
- Fn::Join:
- ''
- - 'arn:aws:s3:::cs-'
- Ref: CSExternalID
- "/*"
Roles:
- Ref: CHAOSSEARCHRole
Outputs:
RoleARN:
Description: The ARN of the new CHAOSSEARCH Role
Value:
Fn::GetAtt:
- CHAOSSEARCHRole
- Arn
S3Bucket:
Description: The name of the CHAOSSEARCH S3 bucket that was created
Value:
Ref: CSBucketNameUpdated 9 months ago
